iFixOmaha Blog - Omaha Electronics Repair - ifixomaha.com | Virus Removal: 10 Signs Your PC Has a Virus You Need Removed
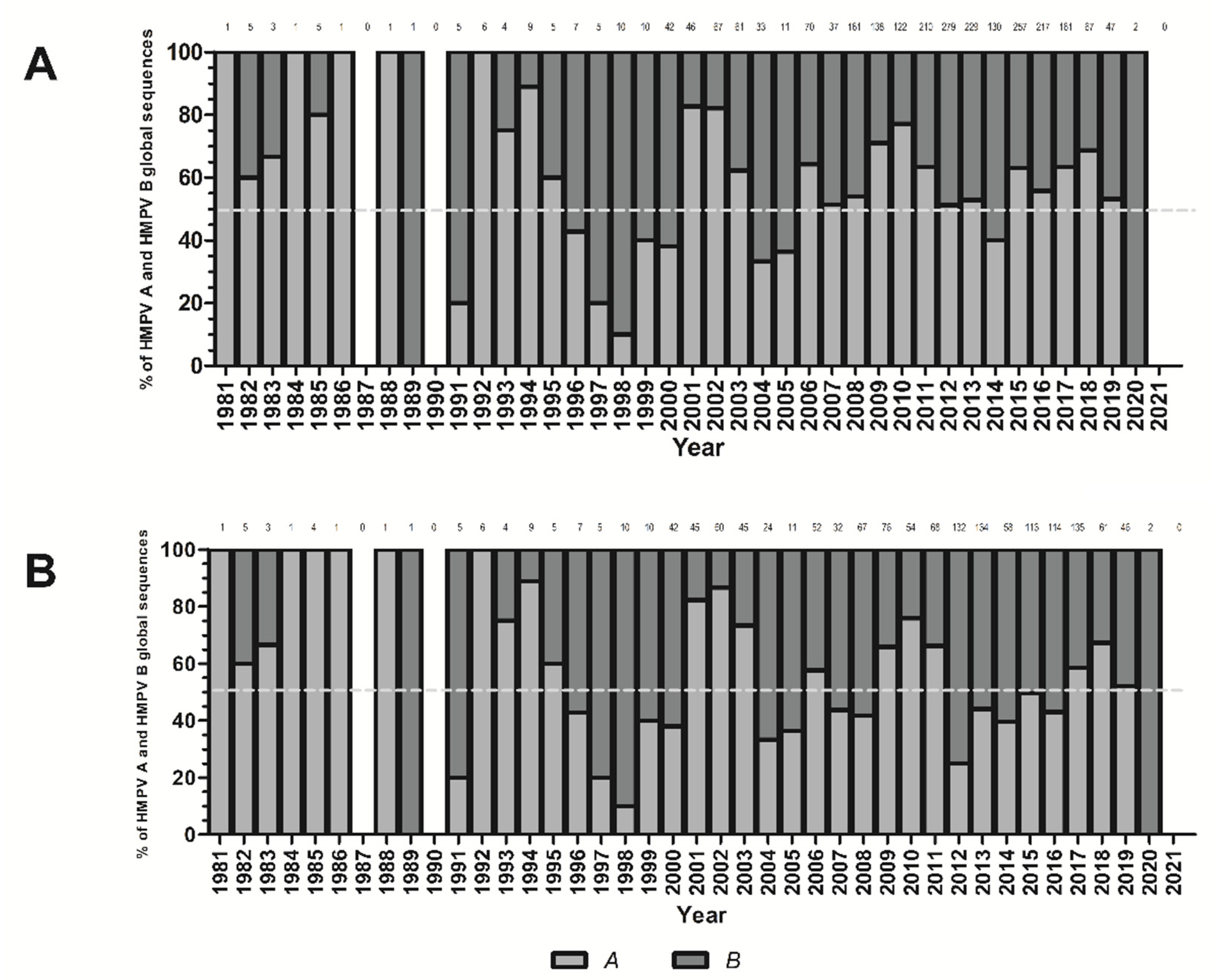
Viruses | Free Full-Text | Global Extension and Predominance of Human Metapneumovirus A2 Genotype with Partial G Gene Duplication

Singapore Police Force on X: "Have you heard of cryptojacking? Cryptojacking is the unauthorised use of a computer or mobile phone by cybercriminals to mine for digital money known as cryptocurrency. Cryptomining

Browser extensions, video downloaders found infected with viruses, if you have these in Chrome, uninstall now
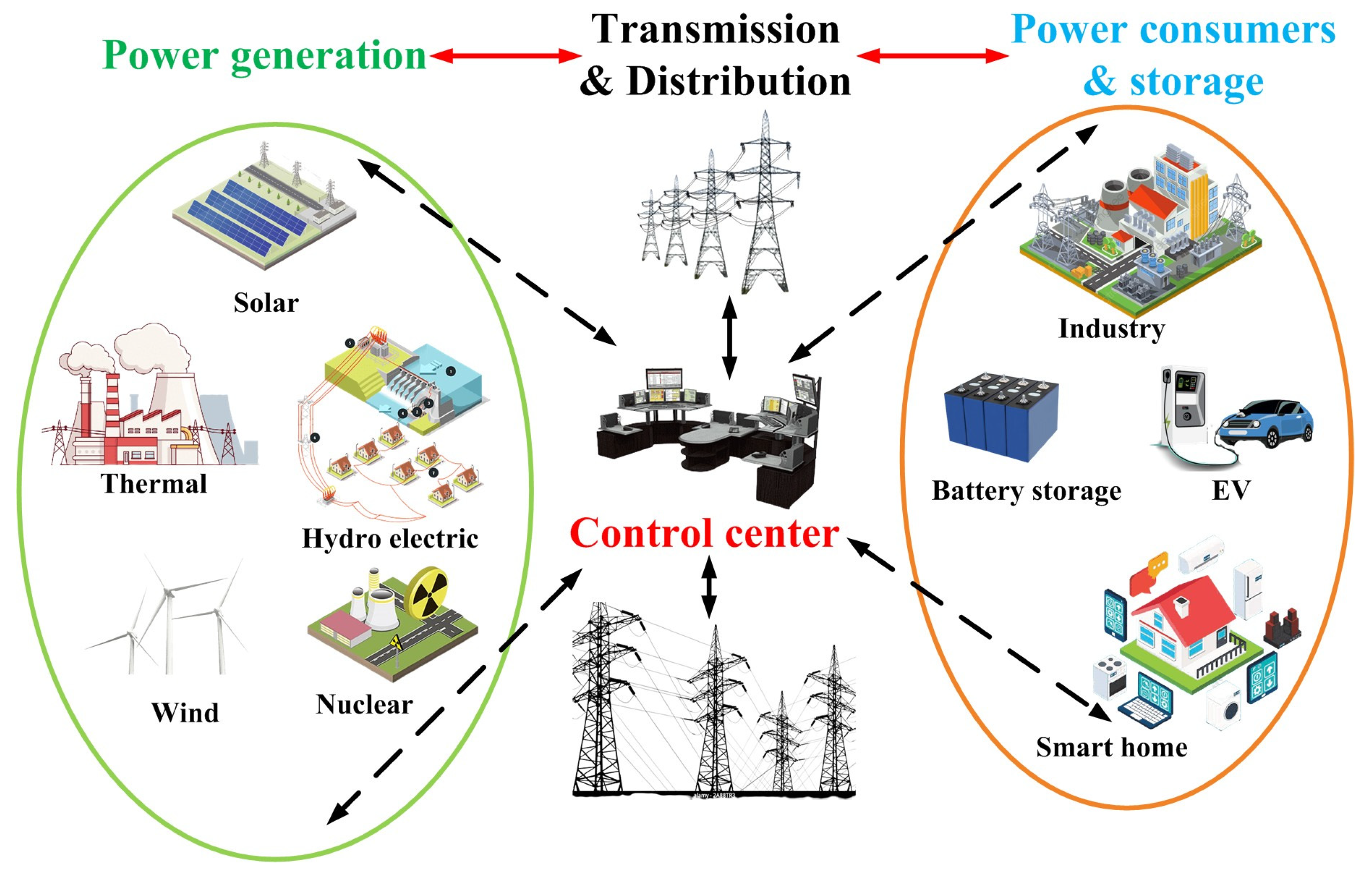
Energies | Free Full-Text | Cyber Attacks in Cyber-Physical Microgrid Systems: A Comprehensive Review
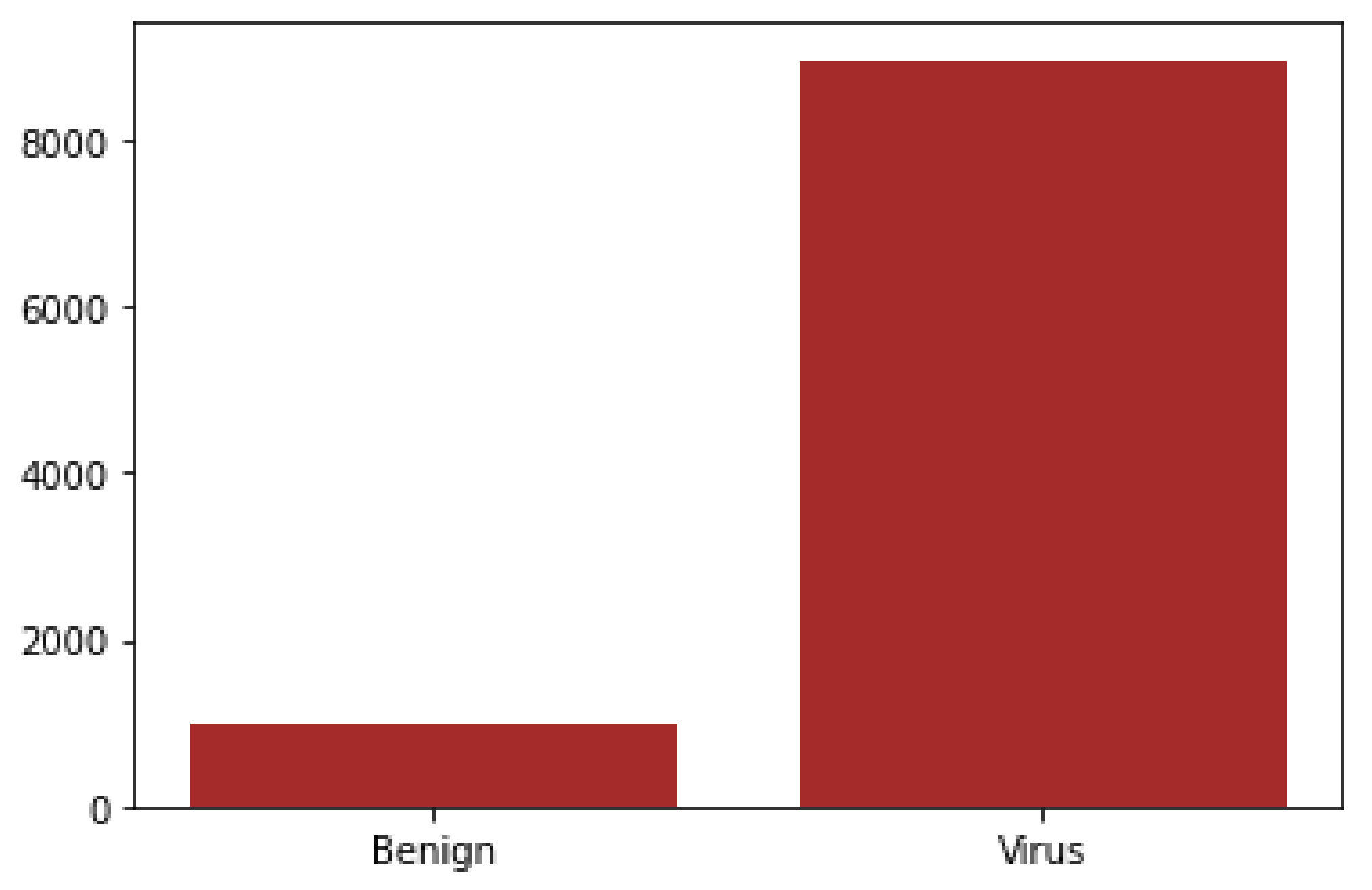
Electronics | Free Full-Text | Detecting the Presence of Malware and Identifying the Type of Cyber Attack Using Deep Learning and VGG-16 Techniques




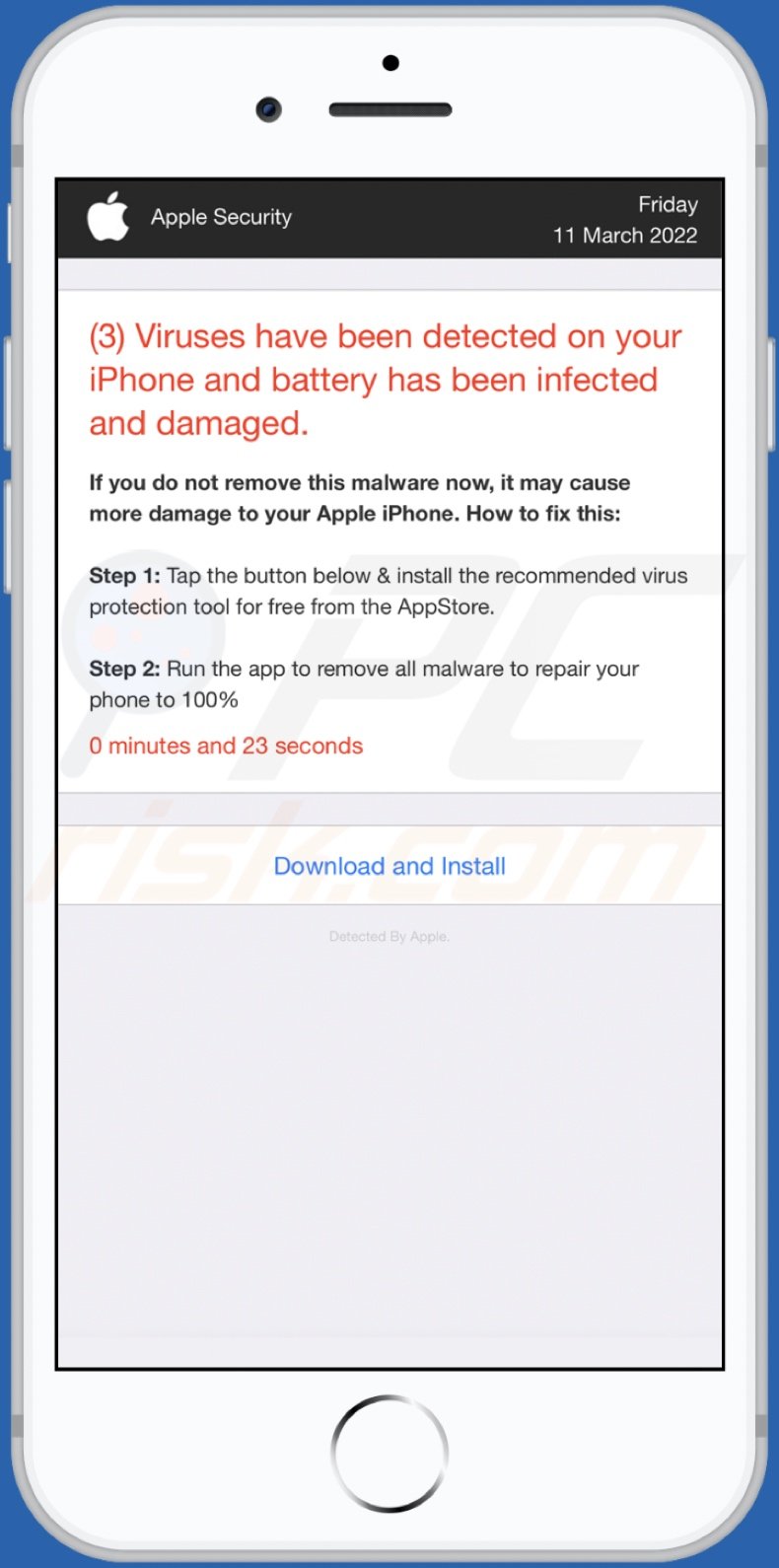


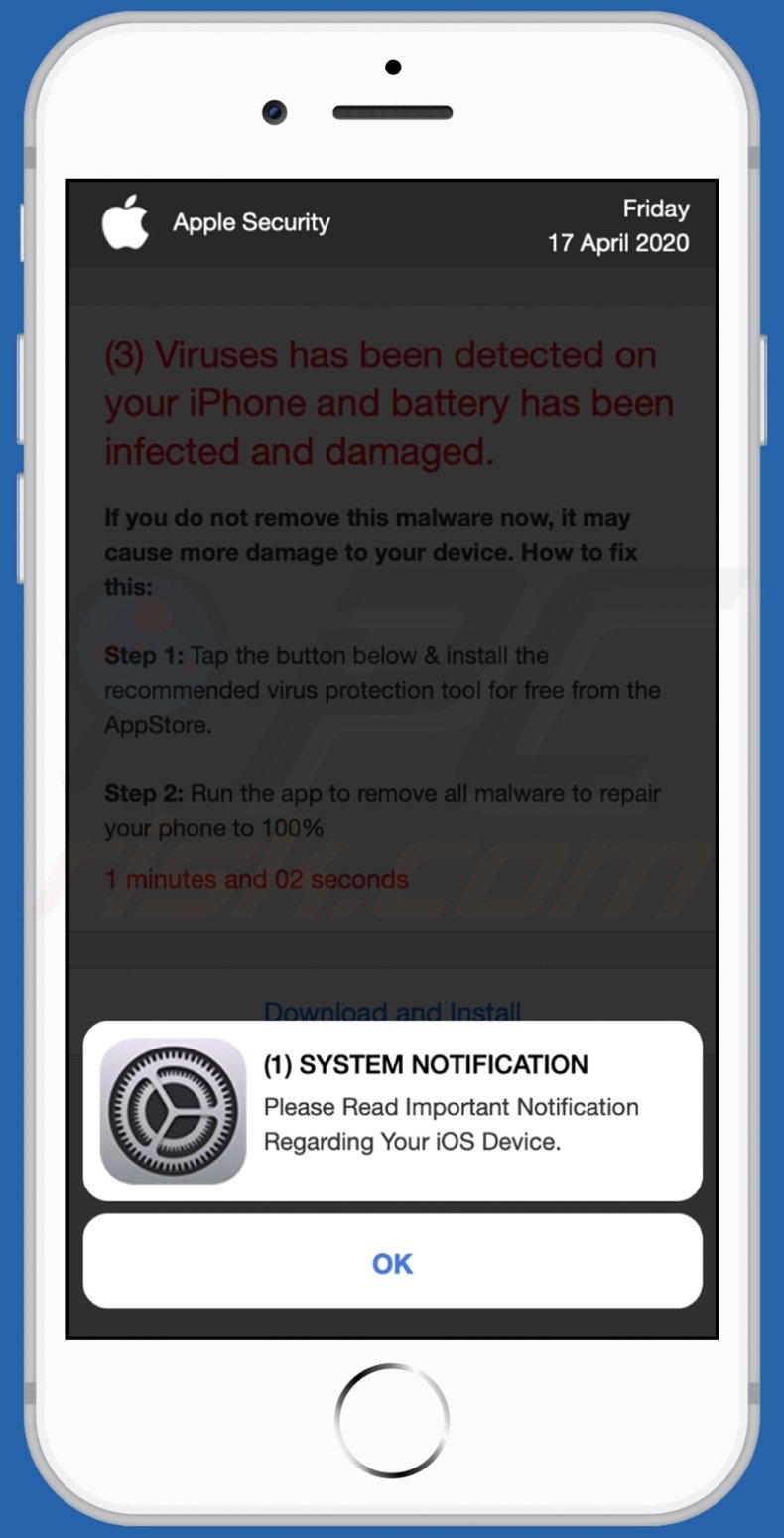
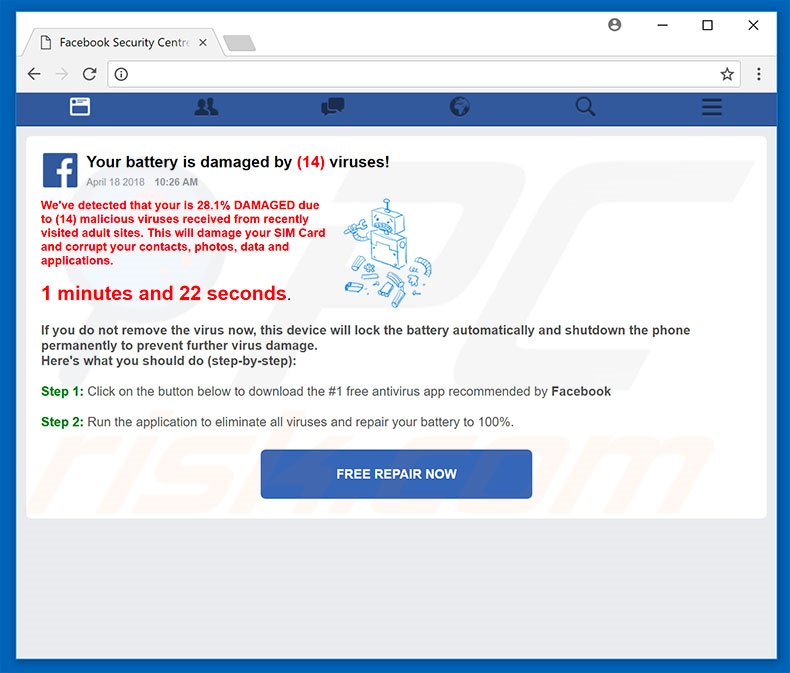
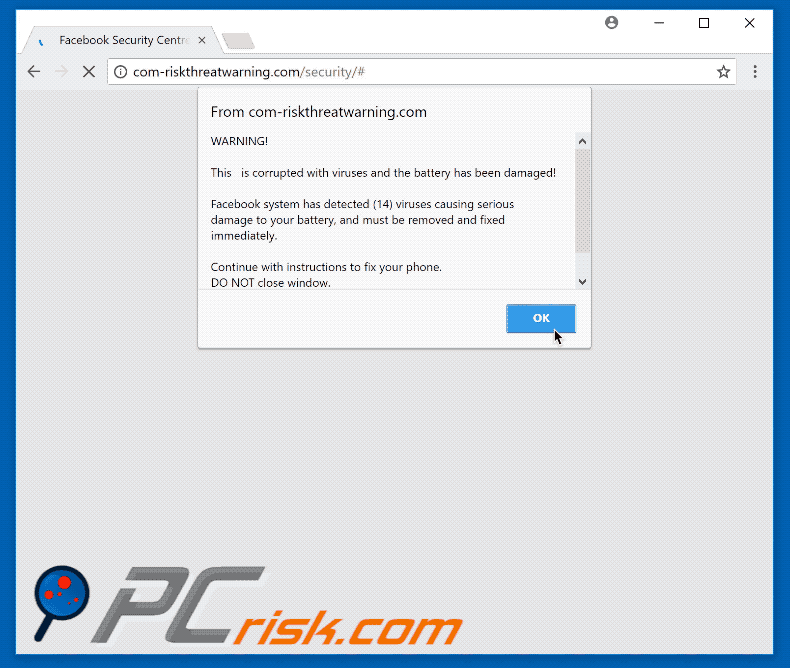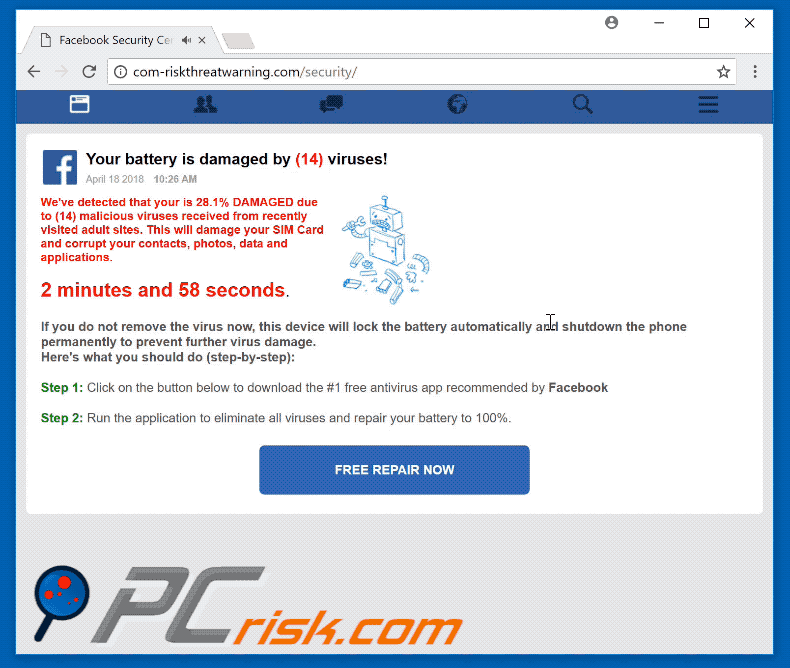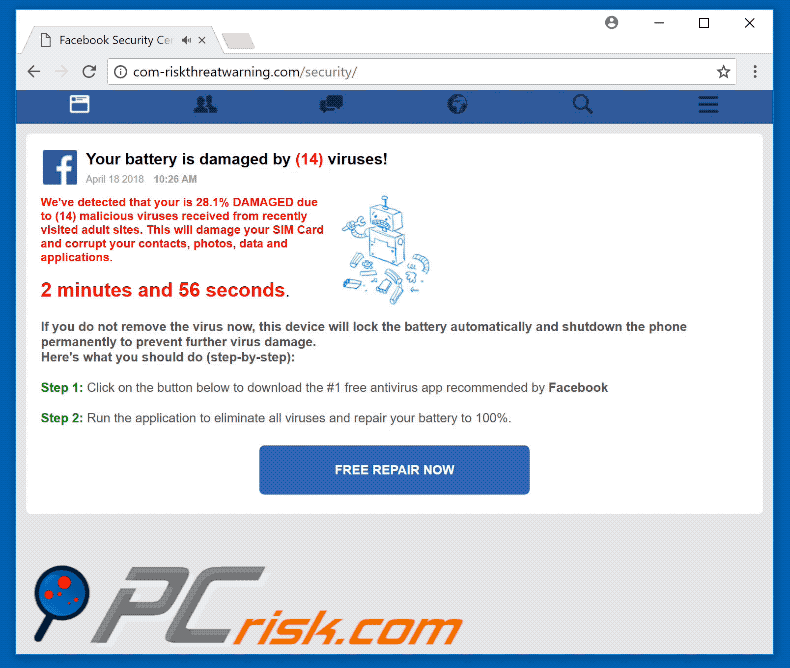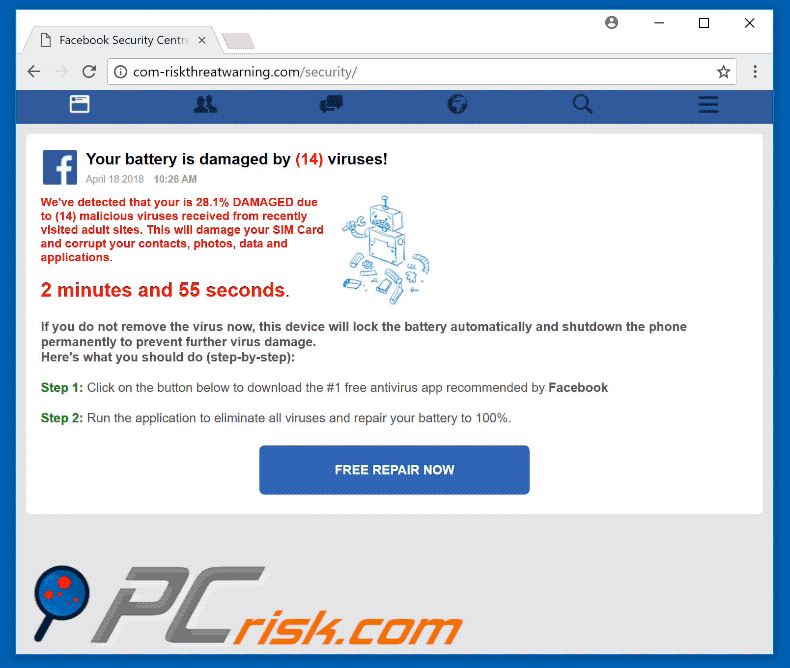
![Remove "Your Battery Is Damaged By Viruses" Pop-ups [Guide] Remove "Your Battery Is Damaged By Viruses" Pop-ups [Guide]](https://malwaretips.com/blogs/wp-content/uploads/2023/09/battery-fake-virus.jpeg)