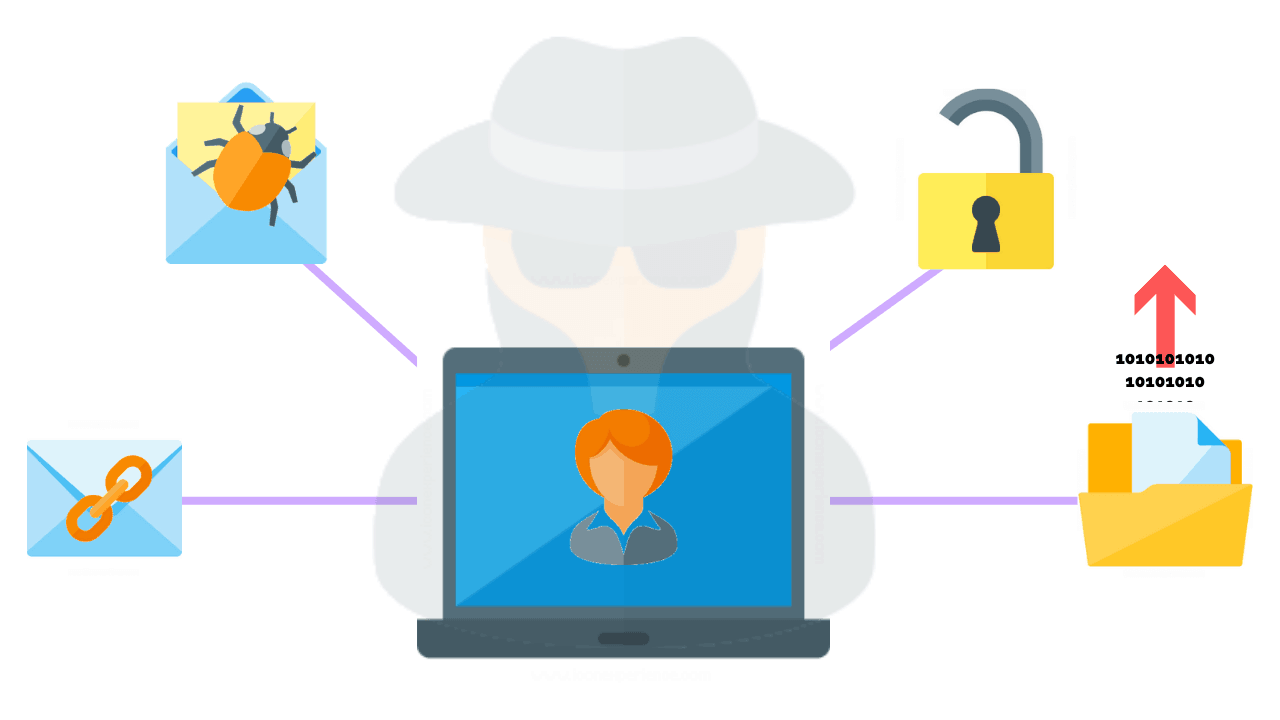
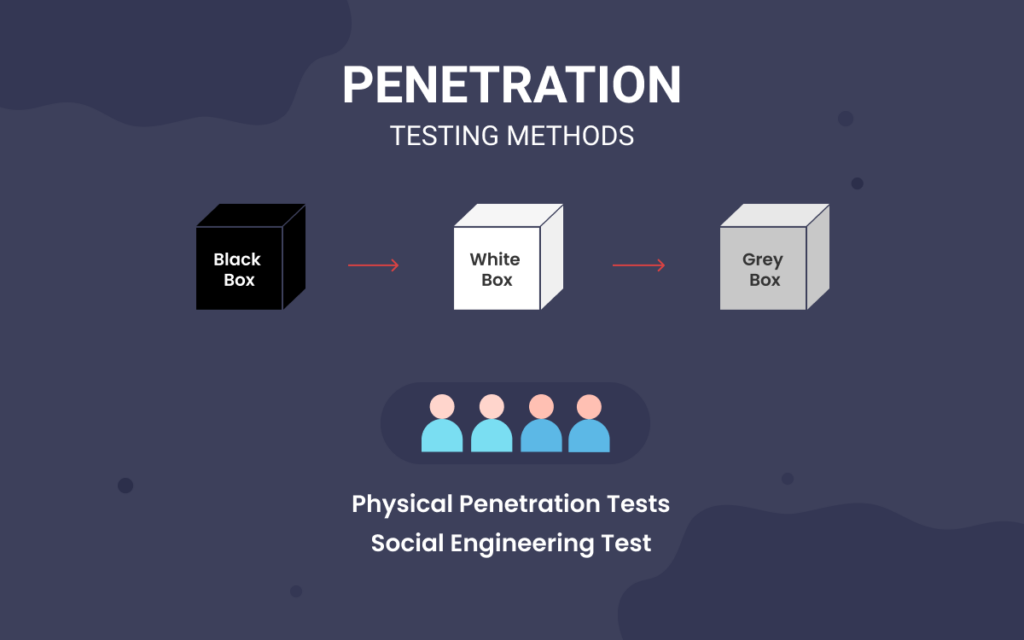
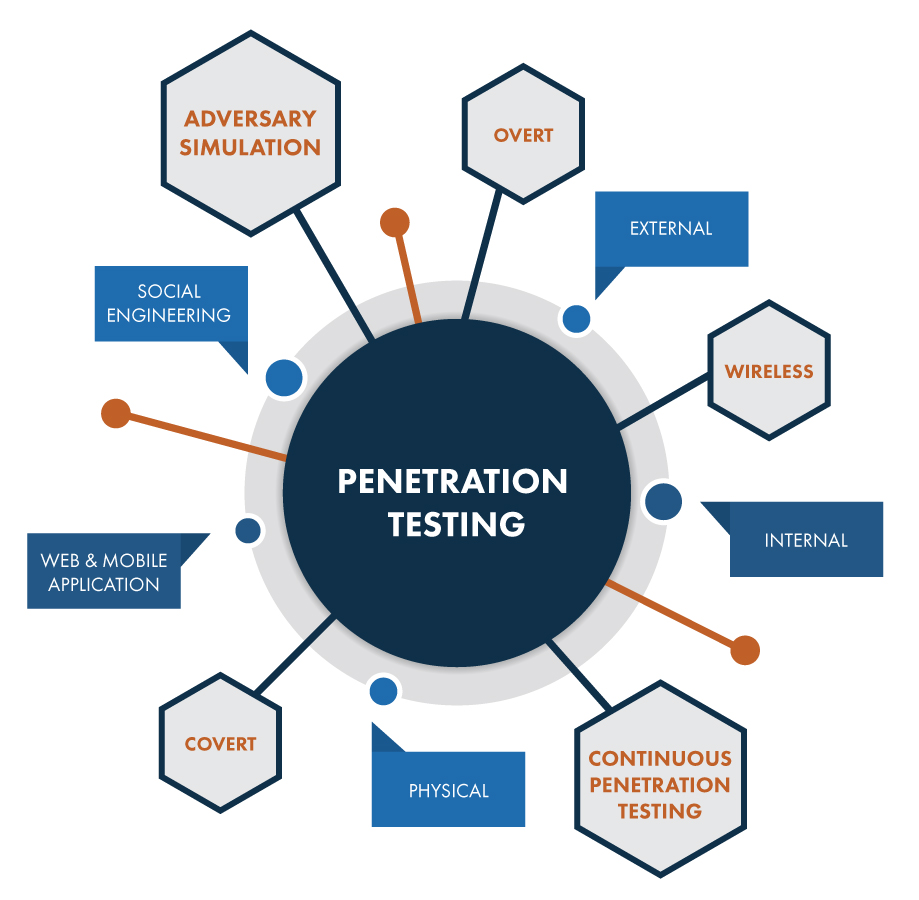
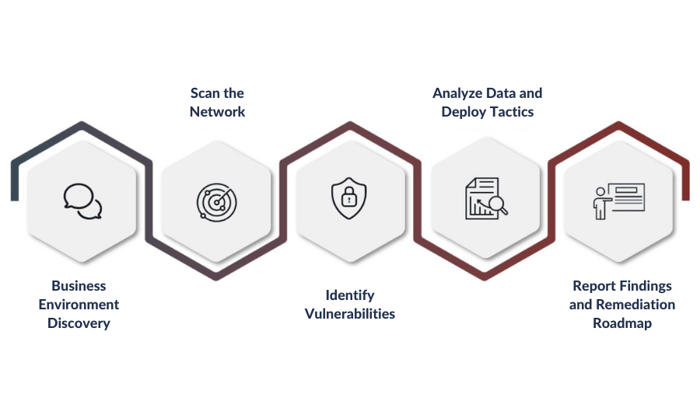
Steps of social engineering penetration testing | Mastering Machine Learning for Penetration Testing

Webopedia - From our friends at eSecurity Planet: Penetration testing: the DIY basics in 7 steps -- Think of internal penetration tests as walking around your house and making sure you haven't

Social Engineering Attacks: A Look at Social Engineering Examples in Action - Hashed Out by The SSL Store™

Social Engineering Penetration Testing: Executing Social Engineering Pen Tests, Assessments and Defense: 9780124201248: Computer Science Books @ Amazon.com